O Discover privileged accounts on systems devices and applications for subsequent management. Previously CA Technologies appeared in the Leader quadrant for the Gartner 2018 Privileged Access Management Magic Quadrant.
The PAM Client is created using a customized Chromium Browser with local Java components to allow local access.

Ca pam privileged access management. Durch die Implementierung einer Privileged Access Management-Lösung wird der privilegierte Zugriff auf Ihre geschäftskritischen Systeme Anwendungen und. PAM ist eine umfassende Cyber-Sicherheitsstrategie rund um Mitarbeiter Prozesse und Technologie zur Kontrolle Überwachung Sicherung und Prüfung aller menschlichen und nicht menschlichen privilegierten. Symantec Privileged Access Management can minimize the risk of data breaches by continually protecting sensitive administrative credentials controlling privileged user access and monitoring and recording privileged user activity across virtual cloud and physical environments.
Zero Trust erfordert die Kontrolle des Zugriffs und privilegierte Zugriffskonten können große Sicherheitsrisiken verursachen. The solution is quick to deploy easy to maintain and can process and record significantly more simultaneous requests with a. Briefly its definitive authorized access of a user process or computer to a protected resource.
O Automatically randomize manage and vault. Success with CA PAM. PAM enables centralized management of local and remote high-risk users in physical virtual and cloud environments.
PAM tools help organizations provide secure privileged access to critical assets and meet compliance requirements by managing and monitoring privileged accounts and access. Layer7 Privileged Access Management controls privileged access across all IT resources including in the cloud. It helps enable your IT teams IT Admins IT Security IT Audit as well as individual business users to profile the privileged.
Since most common web browsers no longer support the us of Java Applets the CA PAM client became a more common way to use the product. The CA PAM client is not much different than the common browser interface. To achieve these goals PAM solutions typically take the credentials of privileged accounts ie.
Stolen admin accounts enable. CA Privileged Access Manager Implementation Services CA Privileged Access Manager CA PAM implementation services put you on a faster path to value via an initial solution deployment that provides a network-based appliance that controls monitors and records the actions of all privileged users. Unternehmen setzen auf Privileged Access Management PAM um sich vor Gefahren im Zusammenhang mit dem Diebstahl von Anmeldedaten und Missbrauch von Privilegien zu schützen.
For all use cases. Stolen admin accounts enable attackers. The product enables you to secure access to critical infrastructure for privileged and third-party users by combining access control and privileged credential management.
PAM tools offer features that enable security and risk leaders to. Customizable and adaptive access policies reduce the verification burden on authorized. Privileged Access Management PAM refers to a class of solutions that help secure control manage and monitor privileged access to critical assets.
Compare Privileged Access Management Software with customer reviews pricing and free demos. The solution also protects privileged identities from attack and. Privileged Access Management Software for your organization.
Privileged access management PAM is a system that assigns higher permission levels to accounts with access to critical resources and admin-level controls. The admin accounts and put them inside a secure repository a vault isolating the use of privileged accounts to reduce the risk of those credentials being stolen. Privileged Access Manager is an automated solution for privileged access management.
IT security breaches are all too common as are attacks using stolen credentials of those with privileged permissions. Was ist Privileged Access Management PAM. CA Privileged Access Manager PAM is an identity and access management IAM product which controls audits and records access to managed devices such as servers instances switches and so on.
You can manage the. Follow the steps in our PAM checklist to plan your strategic journey to privileged access security. Centralize identity through Okta to confidently verify and authenticate users for privileged-account access via SSO and MFA.
Broadcom appeared in the KuppingerCole 2020 Leadership Compass as a Leader. Privileged Access Management therefore encompasses a broader realm than Privileged Account Management focused on the special requirements for managing those powerful accounts within the IT infrastructure of an organization. To make sure you are ready to start your privileged access journey Thycotic has created this FREE PAM Privileged Access Management Checklist to help you build a strong foundation as you move forward.
PAM is based on the principle of least privilege which is crucial to modern cybersecurity best practices. Okta works with Privileged Access Management PAM partners to provide secure user-friendly authentication and account provisioning.
 Ca Pam Integration With Sso Symantec Access Management
Ca Pam Integration With Sso Symantec Access Management
 Unable To Access Web Gui In Ca Pam Symantec Privileged Access Management
Unable To Access Web Gui In Ca Pam Symantec Privileged Access Management
 Unable To Access Web Gui In Ca Pam Symantec Privileged Access Management
Unable To Access Web Gui In Ca Pam Symantec Privileged Access Management
 How To Connect To Ca Privileged Access Manager
How To Connect To Ca Privileged Access Manager
 Ca Privileged Access Manager Coreblox
Ca Privileged Access Manager Coreblox
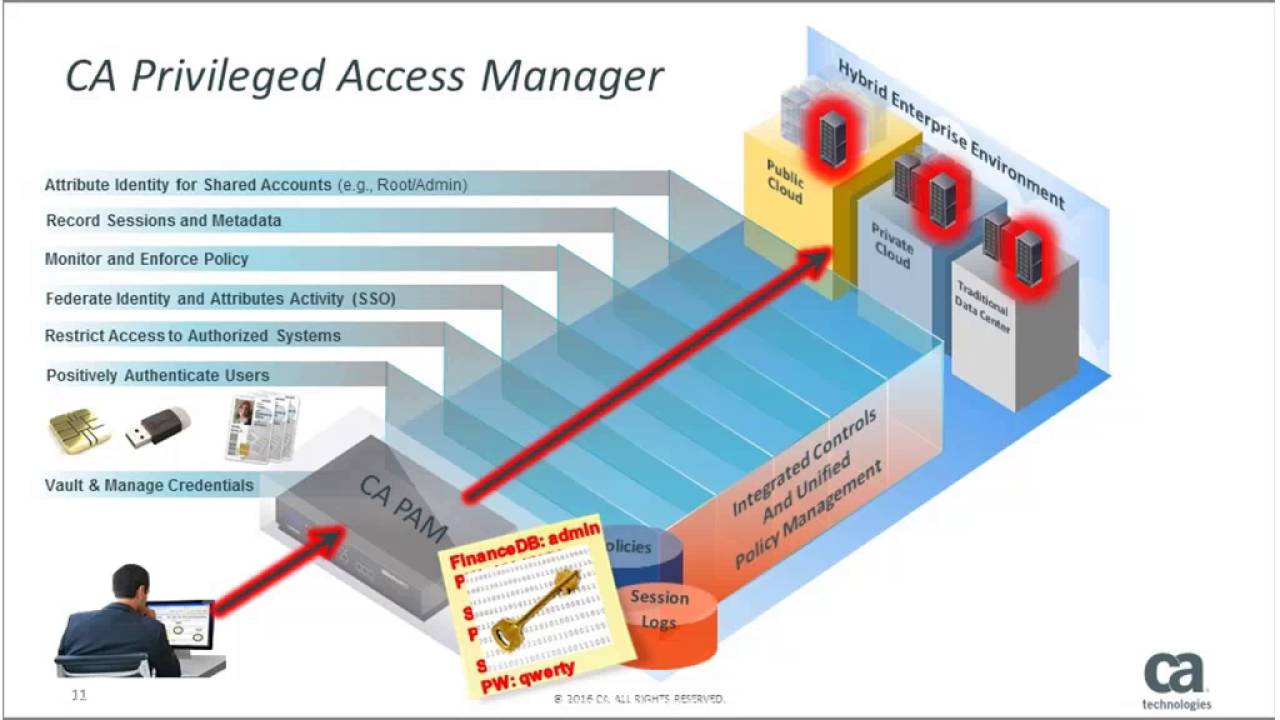 What Is Ca Privileged Access Manager Definition From Whatis Com
What Is Ca Privileged Access Manager Definition From Whatis Com
 Integrate With Ca Privileged Access Manager
Integrate With Ca Privileged Access Manager
Https Www Devconnectprogram Com Filemedia Download 72f0b8c4 7c1c 42df A47c B59c5f0623d9
 Configure Policies To Provision User Access To Devices And Applications
Configure Policies To Provision User Access To Devices And Applications
 Ca Privileged Access Manager In The Modern Software Factory Youtube
Ca Privileged Access Manager In The Modern Software Factory Youtube
 Ca Pam Introduction Video Youtube
Ca Pam Introduction Video Youtube
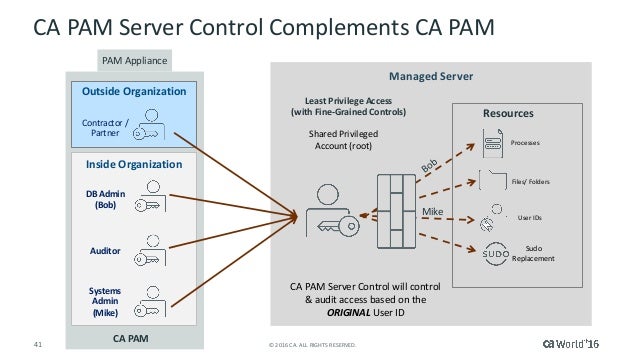 Tech Talk Defense In Depth Privileged Access Management For Hybrid E
Tech Talk Defense In Depth Privileged Access Management For Hybrid E
 Ca Technologies Scales Up Privileged Access Management For Large Enterprise And Managed Service Deployments Business Wire
Ca Technologies Scales Up Privileged Access Management For Large Enterprise And Managed Service Deployments Business Wire


No comments:
Post a Comment
Note: Only a member of this blog may post a comment.