The Threat Visualizer is Darktraces unique 3D graphical interface providing total visibility of all network activity including both traditional and non-traditional IT. From the menu click Config.
Https Www Darktrace Com It Resources Wp Cyber Ai Antigena Email Pdf
Microsoft is partnering with Darktrace a leading autonomous cyber security AI company that uses self-learning artificial intelligence to respond to threats at machine speed.
Darktrace threat visualizer login. This information is processed by the platform and the output is exposed in the Darktrace Threat Visualizer. Darktrace Threat Visualizer UI Build Jun 25 2019. All of the related Darktrace Customer Portal pages and login addresses can be found along with the darktrace customer portals addresses phone numbers.
Since internal threats remain a problem this benefit alone helps to identify slow stealthy attacks especially when the user is unaware such an event. Darktrace Threat Visualizer. The Darktrace Mobile App is a brand new way to experience the Darktrace Threat Visualizer and benefit from the unparalleled threat detection and.
Business executives can use the Dynamic Threat Dashboard and global map. During the POV you will also receive detailed updates on what Darktrace detects produced by world-leading cyber analysts. Caps lock is on.
The business which was founded in Cambridge UK in 2013 provides best-in-class cyber AI to protect organisations against attacks of all kinds including insider threats espionage supply chain attacks phishing. Darktrace Customer Portal. 3D visualization of entire network topology Real-time global overview of enterprise threat level Intelligently clusters anomalies Pan-spectrum viewing higher-order network topology.
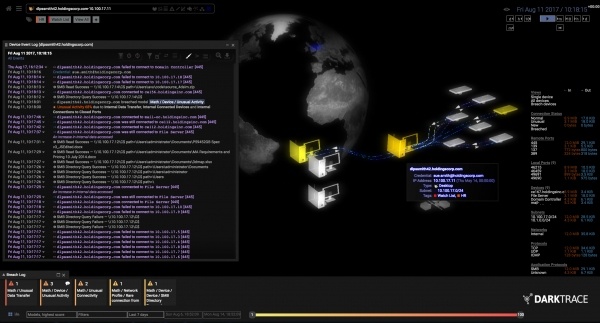
Darktrace customer portal portal pages are updated regularly by the darktrace. The Threat Visualizer is Darktraces graphical and interactive 3D interface which enables analysts and business executives to intuitively visualize behaviors and investigate anomalies without requiring an understanding of the advanced mathematics that power the platform. Set JSON Syslog Alerts to True.
Organise for a SPAN port mirror to be configured at your core switches 2. With ransomware attacks against AXA ASIA Colonial Pipeline and Irelands Health Service last week this blog explores how cyber-criminal groups are exfiltrating data to coerce victims into paying in what is known as double extortion ransomware. Our team will be in touch shortly.
To send data from Darktrace use the settings in our Threat Visualizer change the following Config settings. IP address of the computer the Splunk app is installed on. The device event log graphing function advanced search and packet capture analysis.
The Threat Visualizer is designed for users with varying levels of experience. Review the visualizer tool connection log options and learn how Darktrace conducts Deep Packet Inspections. Darktrace Installation Guide 1.
Darktraces cyber AI technology defends the digital infrastructures of thousands of organizations across more than 100 countries. Darktraces experienced team will install an appliance within your environment in just one day and give you access to the groundbreaking Threat Visualizer interface. Threat Visualizer 30.
Threat Visualizer The Threat Visualizer is Darktraces graphical and interactive 3D interface which enables analysts and business executives to intuitively visualize behaviors and investigate anomalies without requiring an understanding of the advanced mathematics that power the platform. Darktrace appliances ingest network data into one or more packet capture ports. The Darktrace Mobile App is a brand new way to experience the Darktrace Threat Visualizer and benefit from the unparalleled threat detection and visibility that Darktraces Enterprise Immune System offers from wherever you are.
The platform surfaces abnormalities within the customers network into a threat tray from which threats are triaged using four key tools. DarkTrace Threat Visualizer takes the recognition of past behavioral changes into account providing a resource for identifying the potential vulnerabilities that arise from within the system. Darktraces Threat Visualizer leverages the Enterprise Immune System technology to represent global enterprise network activity in a manner that is designed for use by both C-level executives and threat analysts.
Full access to the Darktrace Threat Visualizer and three bespoke Threat Reports with no obligation to purchase. Specific clusters subnets and host events. Thank you for booking a 30-day trial with Darktrace.
The Threat Visualizer can be accessed from any device via a web browser and is touch-pad friendly. Using Darktrace Advanced. Threat Visualizer Part 2 Investigation The second part of this course complements learning from the familiarization class and engages more advanced Threat Investigation and Optimization topics including.
The links for the darktrace customer portal Portal have been listed below. In the increasingly complex threat landscape the Threat Visualizer will use the underlying Bayesian algorithms to dynamically.
